Objective 6: Splunk Challenge
The Sixth Objective involved utilizing a splunk environment to sift through log events. These logs were mostly generated through the means of Splunk's own "Mitre ATT&CK Framework Simulation" scripts, known as the Splunk Attack Range. Through a series of questions, you are to sift through the logs and determine the results of these simulated attacks. For these, I will list the splunk search string I used as well as the answer to the question.
-
How many distinct MITRE ATT&CK techniques did alice emulate?
Using:
| tstats count where index=* by indexAnswer:
13 -
What are the names of the two indexes that contain the results of emulating Enterprise ATT&CK technique 1059.003? (Put them in alphabetical order and separate them with a space):
Using:
| tstats count where index=* by indexAnswer:
t1059.0-03-main t1059-003-win -
One technique that santa had us simulate deals with 'system information discovery'. What is the full name of the registry key that is queried to determine the MachineGuid?
Using:
index=t1082* MachineGUIDAnswer:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Cryptography -
According to events recorded by the Splunk Attack Range, when was the first OSTAP related atomic test executed?
Using:
index=attack "Test Name"="Download a File with Windows Defender MpCmdRun.exe"Answer:
2020-11-30T17:44:15Z -
One Atomic Red Team test executed by the Attack Range makes use of an open source package authored by frgnca on Github. According to Sysmon (event code 1) events in splunk, what was the processID associated with the first use of this component?
Using:
EventCode=1 index=* NOT splunk WindowsAudioDevice-Powershell-CmdletAnswer:
3648 -
Alice ran a simulation of an attacker abusing Windows registry run keys. This technique leveraged a multi-line batch file that was also used by a few other techniques. What is the final command of this multi-line batch file used as part of this simulation?
Using:
index=t1547* .bat NOT batstartupAnswer:
quser -
According to x509 certificate events captured by Zeek (formerly Bro), what is the serial number of the TLS certificate assigned to the Windows domain controller in the attack range?
Using:
index=* sourcetype=bro* sourcetype="bro:x509:json"Answer:
55FCEEBB21270D9249E86F4B9DC7AA60 (was the most used, assumed it was the DC)
Final Challenge:
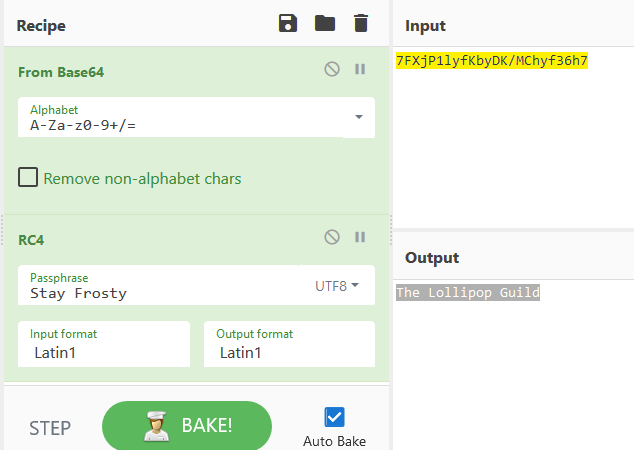
Decrypt this Base64 encoded ciphertext:
*7FXjP1lyfKbyDK/MChyf36h7*
It's a common algorithm that uses a key, and the key is Santa's favorite phrase, taken from Dave Herrald's Splunk Talk: "Stay Frosty"
Using the RC4 Stream Cipher Encryption Algorithm and "Stay Frosty" as the passphrase, I was able to decrypt it to: The Lollipop Guild: